
At JNUC '25 (Jamf Nation User Conference), Nick Vigier (CISO at Oscar Health) shared how the company achieved 65% reduction of outdated MacOS endpoints, eliminating forced reboots and reducing Mac OS version sprawl from 30+ variations to single digits -- all using AI-powered employee engagements.
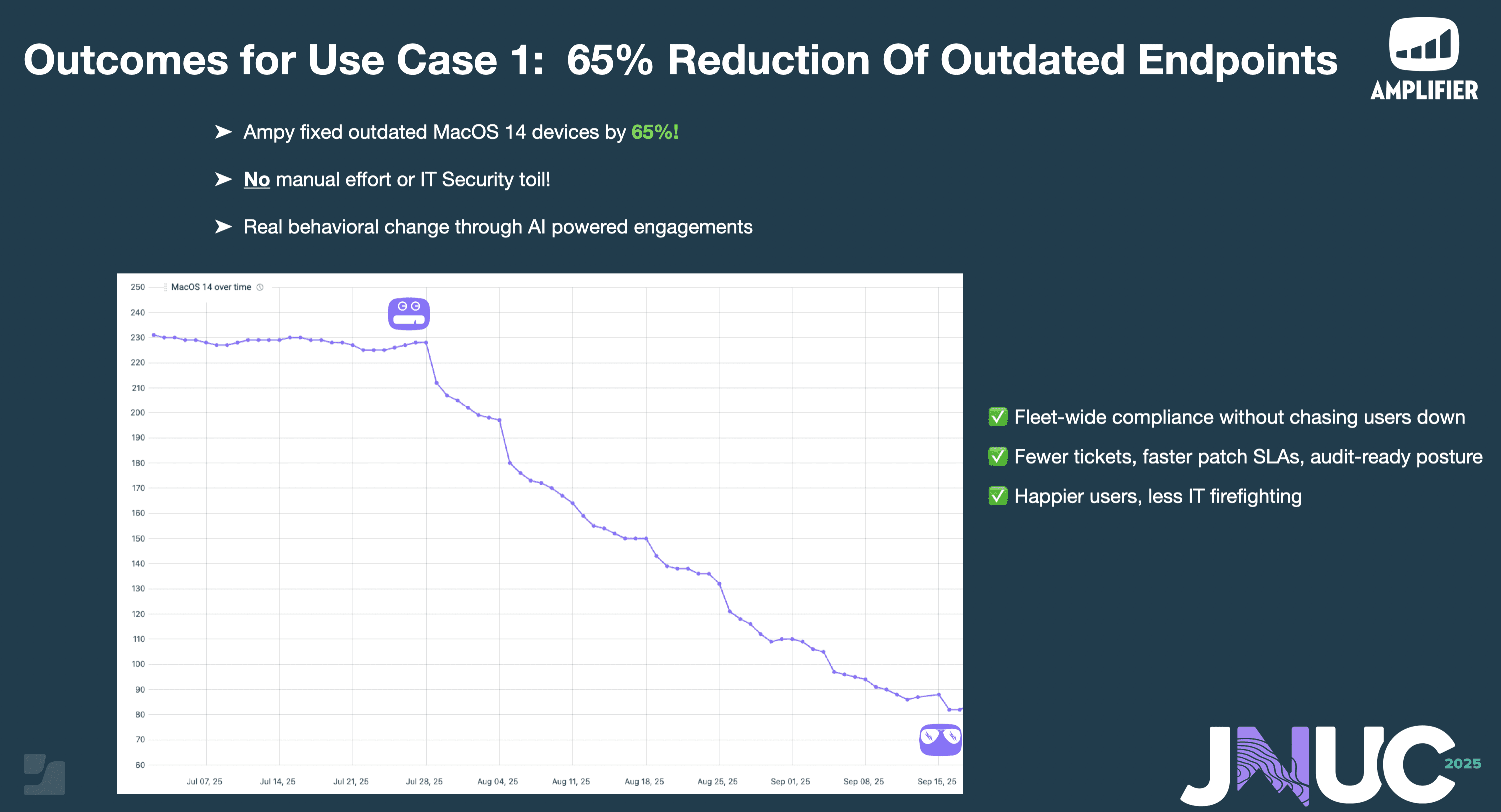
Conversational AI transformed security from "yelling at users via emails" to targeted Slack engagements that met employees where they work. AI unlocks the impossible combination of both automating user security AND amplifying user experience by giving users control over when and how security actions happen.

Nick's team built security culture through curiosity, democratized security, and gamified compliance — eliminating IT toil while improving response times from days to minutes.
Nick spoke about how they democratize security by turning users into part of the fix, and why this approach drove toil reduction for Oscar’s IT & security teams while improving user security hygiene:
"How do we democratize security? "
"As IT and Security teams, we have a lot of knowledge, but we don't communicate those back out to the employees in a way that they can understand and be part of the journey. We're like this mythical scary thing that they don't want to engage with and all we do is yell at them and it's a very negative experience. It's not anything that people want to be a part of. So, how do we turn that dynamic on its head and democratize that?"
"How do we start building a culture of security? A culture of employees wanting to be part of solving our problems, and being able to engage employees with their curiosity."
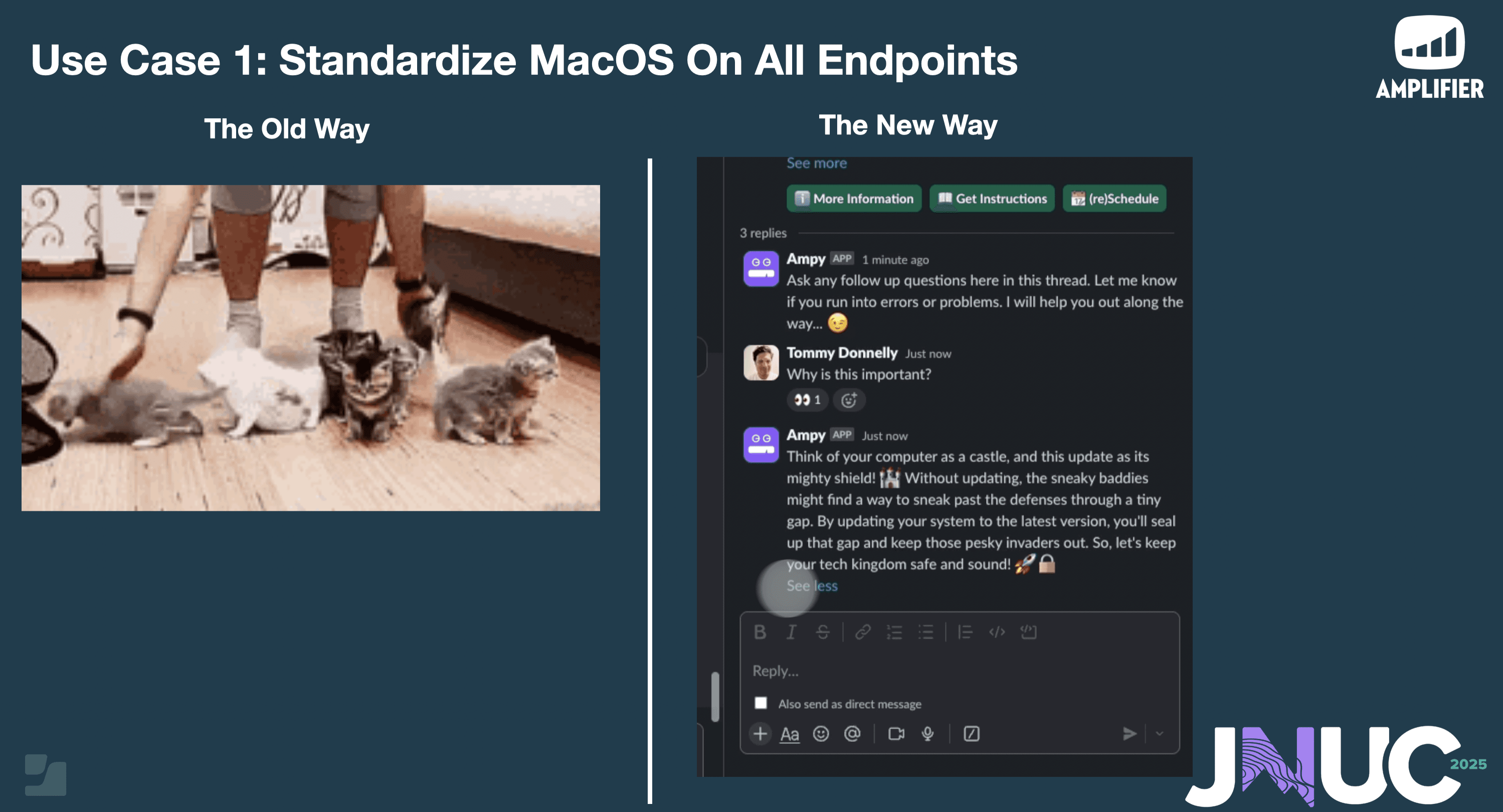
"What usually happens is you find the list of machines that are out of date and then you go and you create a distribution list and BCC everybody and go yell at them about not updating their machine and then they ignore the email and then nothing ever happens, right? "
"And so it becomes this just a terrible game of poor communication, poor user experience, um no empathy whatsoever, and you're not meeting anybody where they are. You're literally just beating them about the face and neck and hoping that they're eventually going to comply, which sucks."
"What we did with Amplifier was instead leveraging Jamf smart groups to target user engagements"
"So, we went from 'how do we herd cats and try to get them into the box' to collaboratively get them to do the thing. Sometimes we get really upset with the cats because they really don't get what we're trying to accomplish, but we're going to get them there eventually, maybe someday, right? And instead what we ended up with were these engagements that we targeted at certain times that really made the difference."
Nick dove into insights on how to run a modern security program:
"We measure our NPS score within the organization,.trying to make sure that people want to engage with us. People are promoters ultimately, right? Then really its that continuous improvement iteration - how do we continue to make this better to show them that it's getting better?
"But then also the back end of that is our toil goes down significantly. They're engaging. They're improving their systems. They're taking accountability and responsibility because we've shared information with them. We're engaging with their curiosity. And then, that becomes a recruiting tool. And now we end up with a more secure organization, a more resilient organization, and people that understand the why"



